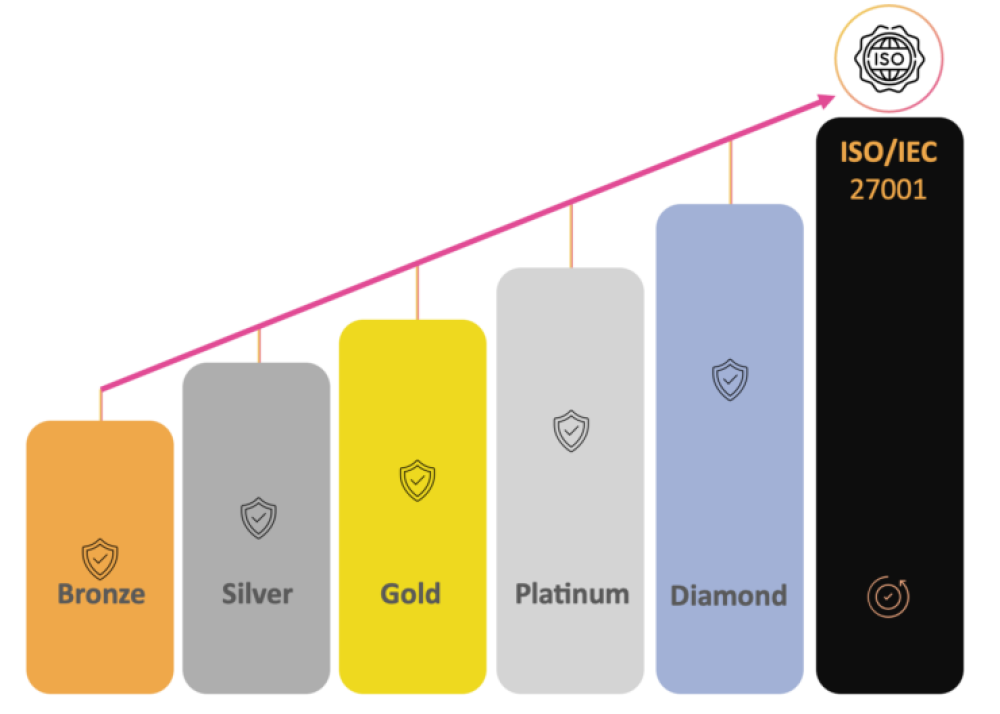
Gold is a good level of cyber maturity, hygiene and policy adoption. Ideal for a SMB that have a matured operation where data is valued.
23 control requirements
Key deliverables, in addition to Bronze-level:
– Certificate that validated business maturity for 12-months
– Patch management on all servers**
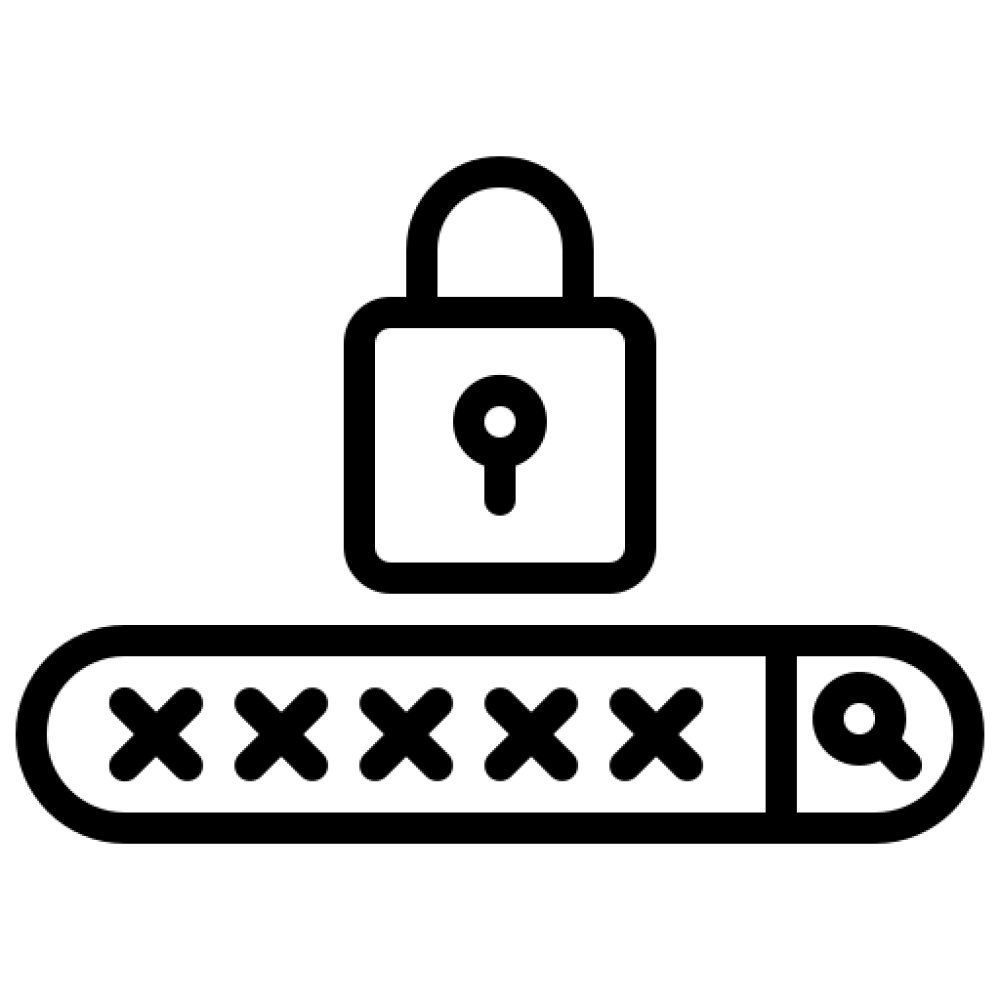
– Multifactor Authentication (MFA) for business applications and social media accounts
– Implemented a cyber security policy
– Implemented a response plan for cyber, backup, business continuity and disaster recovery plans
– Retention lifecycle, Secure methods of physical document destruction
– Device lifecycle, ensure all devices with sensitive, private and/or confidential information are disposed of security
– Regular cyber security awareness training for all employee’s